Secure, flexible and protected around the clock
SOC as a Service - your holistic attack protection with a modern XDR approach
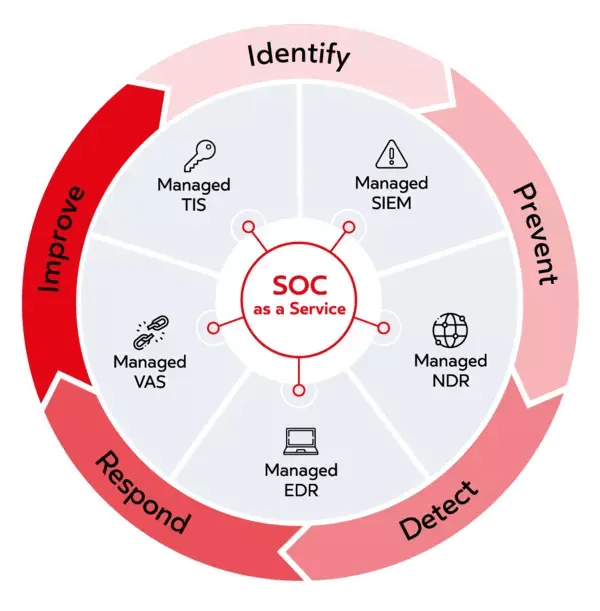
SOC as a service for companies
Your cyber security - professionally managed
Cyber attacks are becoming more frequent, more sophisticated and faster. For many companies, it is a challenge to keep pace with this dynamic. Our SOC as a Service takes this burden off your shoulders: you receive a fully managed security solution that detects, analyzes, and neutralizes threats in real time – around the clock, without the need to build your own team or infrastructure.
This keeps you protected at all times while you can concentrate fully on your core business.
SOC as a service from dacoso
Cyber security - holistic, intelligent, from a single source
Our SOC platform comprises the following modules:

Endpoint Detection & Response (EDR/XDR)
Strong protection - directly on the end device and beyond
With EDR/XDR, you can reliably protect your end devices - from laptops and servers to mobile devices - against modern cyberattacks. The solution continuously monitors all activities, uses AI and behavioral analysis to detect even unknown threats and reacts automatically: affected devices are isolated and attacks are stopped.
Thanks to the extended XDR approach, identities and cloud environments are also included - for holistic detection and defense across all relevant attack surfaces.
Your advantage:
Attacks such as ransomware or zero-day exploits are stopped before they can spread - quickly, intelligently and automatically.
Network Detection & Response (NDR)
Detect attacks in the network before damage occurs
NDR continuously analyzes the data traffic in your network and detects suspicious activities that traditional protection systems often overlook. Through context-based analyses and intelligent pattern recognition, the solution identifies threats at an early stage and automatically initiates countermeasures before attacks can spread or cause damage.
Your advantage:
You retain full control over your network and stop attacks before they become critical.
Security Information & Event Management (SIEM)
Legally compliant, individual and analyzable at any time
SIEM provides you with a powerful solution for long-term storage and evaluation of security-relevant log data - ideal for meeting legal requirements and for rapid forensic analysis in the event of an emergency. In addition, individual detection rules can be defined that are precisely tailored to your organization - including targeted monitoring of business-critical applications. This allows you to maintain an overview at all times, detect threats at an early stage and react in a targeted manner.
Your advantage:
You meet compliance requirements, secure your data in the long term and react quickly and soundly in the event of an emergency.
Advanced Incident Response (AIR)
React quickly, take targeted action and be optimally prepared in an emergency
With AIR, you are not only optimally positioned in an emergency, but also optimally prepared in advance. On request, our service includes structured preparation for potential security incidents - including internal check processes and realistic emergency simulations. If an attack occurs, our incident response experts will be at your side immediately: with forensic analysis, technical containment and professional crisis management. This allows you to minimize damage, preserve evidence and quickly restore business operations.
Your advantage:
You are prepared for security incidents and receive fast, targeted support from experienced specialists in the event of an emergency.
Vulnerability Assessment Service (VAS)
Detect vulnerabilities before they become a risk
With our VAS, you can check your systems regularly and automatically for known and potential vulnerabilities. Every vulnerability discovered is assessed according to its actual risk so that you can take targeted and prioritized action. This allows you to close security gaps before attackers exploit them - efficiently, transparently and without additional effort.
Your advantage:
Your IT infrastructure is proactively secured - without manual checks and nasty surprises during audits.
Threat Intelligence Service (TIS)
Know early on what attackers are planning and take targeted countermeasures
With our TIS, you are always one step ahead of threats. We continuously provide you with up-to-date information on new attack methods, vulnerabilities and threat actors - from trusted sources, global networks and targeted darknet monitoring. This knowledge flows directly into the detection and defense processes of our Security Operations Center (SOC) and strengthens your security strategy in the long term.
Your advantage:
You benefit from global threat knowledge including darknet analyses - without the need for your own research or additional tools.
Why companies rely on SOC as a Service from dacoso
Your benefits at a glance
- 24/7 protection by our experienced SOC team
- Monitoring of your IT and "mission-critical" OT environments, prevention of attacks without compromising availability
- No need to invest in your own infrastructure or personnel
- Simple connection to your existing IT landscape
- Flexible and scalable solution that grows with your company
- Audit- & compliance-ready - meets the requirements of ISO 27001, BSI IT-Grundschutz, NIS-2, GDPR, DORA and other relevant regulations
- Full cost transparency - you retain control at all times
- Flexible module selection: You only book what you really need
Safe from cyberattacks - permanently and reliably
With SOC as a Service from dacoso, you can effectively protect your company from digital threats - 24/7, without your own security team or additional infrastructure. We take over the monitoring, analysis and defense against attacks so that you can concentrate fully on your core business.

How it works
Maximum cyber security in 4 steps
-
Analyze the security situation: Together we analyze your current IT security situation, identify risks, check existing systems and define your individual requirements.
-
Configure the solution: Based on your requirements, we set up your customized SOC-as-a-Service environment - including all relevant protection modules such as EDR, NDR, SIEM, AIR, VAS and TIS.
-
24/7 monitoring & response: Our experienced SOC team monitors your systems around the clock, detects threats at an early stage and responds immediately.
-
Continuous improvement: You receive regular reports, recommendations for action and review appointments. This allows us to continuously develop your security strategy - transparently and measurably.